With the modulation techniques development the mobile communications is being affected so much through the symbols are carrying so huge information in it.
However with this increasing technique there is also a problem called Inter-symbol interference or ISI.
Particularly in telecom ISI is a form of distortion of a signal in which a symbol interferes with other symbols. There can be multiple cause to have this ISI. It can be caused by multipath propagation or the inherent non-linear frequency response of a channel causing successive symbols to "blur" together.
Theoretically a signal receives at receiver without any loss, noise and interference but in real scenarios it does not. It will have multiple delays, multipath propagation and Band Limited channels.
Delay Spread:
A transmitted symbol can be received multiple times at the receiver, more or less as an "echo" effect. This echo is what we call "Delay Spread".
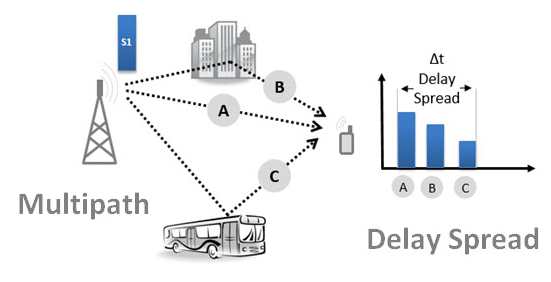
In the above figure, the transmitter transmits a single symbol. This symbol is propagated along different paths (A, B and C), and eventually reaching the receiver at multiple time instants, and therefore with multiple "replication."
The total elapsed time between the first and last is determined by the environment (including the structures, how close they are, etc..). For example, in an urban environment, where the reflection is high (many buildings, many vehicles parked and moving), this delay has a typical value of 5-10 microseconds.
Multipath Propagation:
Due to the signal propagation phenomena, like reflection or diffraction, a receiver can receive several delayed versions of the same signal. This creates Inter-Symbol Interference (ISI).
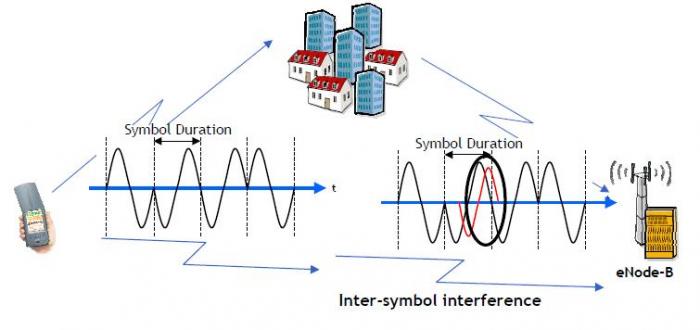
The multi-path impact is an overlapping of 2 symbols, called Inter-Symbol Interference (ISI). The modulation is based on the amplitude and on the phase, so in case of overlapping there are 2 different amplitudes and phases. The receiver is not able to decode the state of the symbol.
The guard time is called the Cyclic Prefix (CP). It permits to facilitate demodulation.
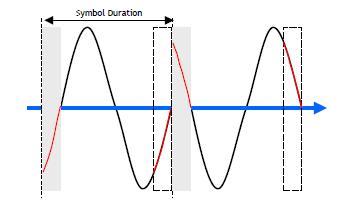
The cyclic prefix transforms the classical channel convolution into a cyclic convolution which permits easy demodulation after FFT.
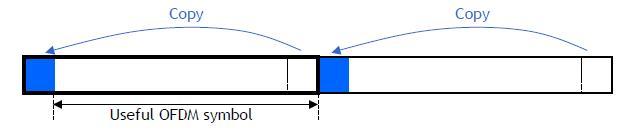
Symbol Duration:
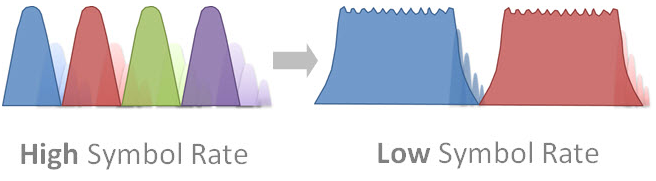
As can we easily conclude, a very important determining factor for the ISI is the time duration of the symbol.
If the symbol period (T) is very short compared to the "Delay Spread" (t) the impact is significant (T << t).
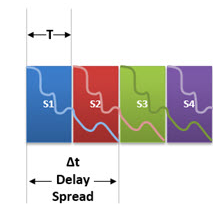
But if we can extend the symbols length, most of them will not suffer the impact of ISI (T >> t).
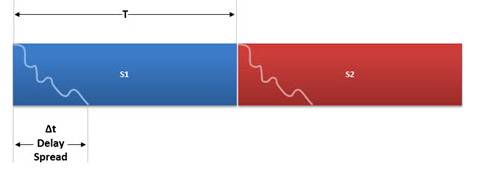
One small part of the symbol will continue to be impacted, but for most of its duration, the symbol will remain not affected by reflections propagated in "Multipath".
That is why the ISI is minimized when we use a higher symbol period (or Lower Symbol Rate).