The Network Access Layer of the TCP/IP model is associated with the Physical Layer (Layer 1) and the Data Link layer (Layer 2) of the OSI model. The Network Access Layer's function is to move bits (0s and 1s) over the network medium.
The OSI Physical layer is responsible for converting the frame into a stream of bits suitable for the transmission medium. The OSI Physical layer manages and synchronizes signals for the actual transmission. On the destination device, the Physical layer reassembles these signals into a data frame.
The OSI Data Link layer is again subdivided into the following two sub layers according to their function:
Media Access Control (MAC) Sublayer :— MAC sublayer provides an interface with the network adapter.
Logical Link Control (LLC) Sublayer :— LLC sublayer is responsible for error-checking functions for frames delivered also responsible for managing links between communicating devices.
Structure of an Ethernet Frame:-
The data packets from Internet Layer is moved to Network Access Layer as it moves down the TCP/IP protocol stack. There is a size limitation for Ethernet Frame. The total size of the ethernet frame must be between 64 bytes and 1,518 bytes (not including the preamble). Network Access Layer Breaks Internet Layer data (IP Datagram) into smaller chunks, if necessary, which will become the payload of ethernet frames. A Frame includes data to be transmitted and also a header and a trailer which contain information that the network adapters on the ethernet need to process the frame.
The total size of the ethernet frame must be between 64 bytes and 1,518 bytes (not including the preamble). A frame shorter than the minimum 64 bytes but with a valid CRC is called as a runt. In most cases, such frames arise from a collision. Any frame which is received and which is greater than the maximum frame size, is called a "giant". A "giant" is longer than 1518 bytes yet have a valid CRC. Both runts and giants are considered as invalid.
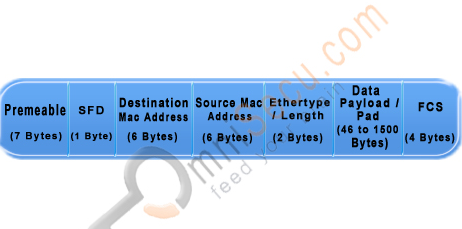
Figure of Structure of an Ethernet Frame
The Ethernet Frame fields are explained below
Preamble: A sequence of 56 bits having alternating 1 and 0 values that are used for synchronization. They serve to give components in the network time to detect the presence of a signal, and being reading the signal before the frame data arrives.
SFD (Start Frame Delimiter): A sequence of 8 bits having the bit configuration 10101011 that indicates the start of the frame.
Source and Destination MAC Addresses: The Source MAC Address is the MAC Address of the device this frame is coming from. The Destination MAC Address is the MAC Address of the device which is going to receive this frame. Both of these fields are 6 bytes long.
MAC address (Layer 2 addresses, physical address or hardware address) is a universally unique identifier, permanently burned in the network card. For Ethernet and Token Ring, these addresses are 48 bits, or six octets (bytes). MAC Addresses are represented in hexadecimal characters because hexadecimal format is easier for humans to read when compared with the binary format. One hexadecimal digit resembles a group of four contiguous binary bits, called a nibble. An example representation of MAC address is AA.F0.C1.E8.13.40.
Length/Type: A 2-byte (16-bit) field contains the number of bytes in the Data field or the nature of the MAC client protocol.
Data: This field contains the actual data transferred from the source device to the destination device. The maximum size of this field is 1500 bytes. If the size of this field is less than 46 bytes, then use of the subsequent "Pad" field is necessary to bring the frame size up to the minimum length.
Pad: If necessary, extra data bytes are appended in this field to bring the frame length up to its minimum size. A minimum Ethernet frame size is 64 bytes from the Destination MAC Address field through the Frame Check Sequence.
Frame Check Sequence: This field contains a 4-byte Cyclic Redundancy Check (CRC) value used for error checking. When a source device assembles a frame, it performs a Cyclic Redundancy Check (CRC) calculation on all fields in the frame except the Preamble, SFD (Start Frame Delimiter), and frame check sequence using a predetermined algorithm. The source device stores the value in this field and transmits it as part of the frame. When the frame is received by the destination device, it performs an CRC test again using the same algorithm. If the CRC value calulated at the destination device does not match the value in the FCS (Frame Check Sequence) field, the destination device will discards the frame, considering this as a transmission error.
To view the MAC Address when you are working with a Windows workstation, run cmd (Start > run > type cmd and Enter). Type the command "ipconfig /all" in the prompt and Enter. Do remember to remove double quotes.
In TCP/IP Network Access Layer lesson, you have learned the sublayers of Datalink Layer. The sublayers of Datalink layer are Media Access Control (MAC) sublayer and Logical Link Control (LLC) sublayer. You also learned about the Ethernet Frame Header, the structure of an Ethernet Frame, different fields in Ethernet Frame header, what is a runt frame and what is a giant frame.



